Hotlink Protection Setup
Overview
To protect your images or other files from being hotlinked on another website, you may use hotlink protection. Hotlinking is the use of an image of the file on another server by pulling the source image from the original server. This uses the bandwidth of your Bluehost account. It appears as though your images are on the other website even though the source is pulling from your Bluehost account. Hotlink protection stops this type of leeching or bandwidth theft.
Using HotLink Protection
Setting up hotlink protection is easy by using the Hotlink Protection tool built into the cPanel.
How to set up Hotlink Protection
- Log in to your Bluehost cPanel account.
- Under the Security section, click the Hotlink Protection icon.
Fields
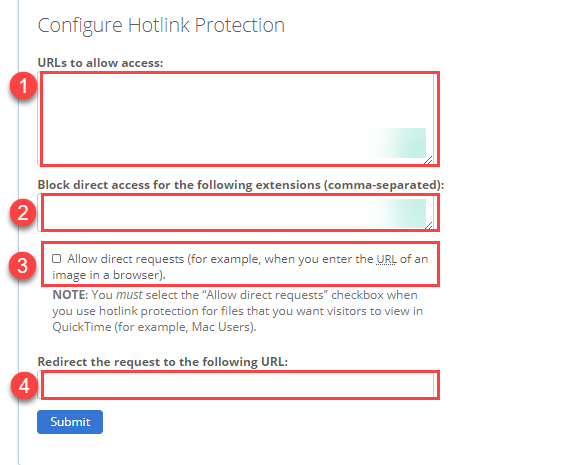
- URLs to Allow Access - Enter the URLs you want to give access to the restricted files. Make sure you enter these with and without the www's if you want the images to be accessed both ways.
- Block direct access for these extensions - Enter the file extensions you want to block access from sites not listed in your URLs to Allow Access list.
- Allow direct requests - Check this if you want to allow people to be able to access restricted files by entering the path/URL into the browser.
- Redirect request to this URL - If you do not have direct requests enabled, entering a URL here will redirect people if they enter the URL of the file directly into the browser.
If you need further assistance, feel free to contact us via Chat or Phone:
- Chat Support - While on our website, you should see a CHAT bubble in the bottom right-hand corner of the page. Click anywhere on the bubble to begin a chat session.
- Phone Support -
- US: 888-401-4678
- International: +1 801-765-9400
You may also refer to our Knowledge Base articles to help answer common questions and guide you through various setup, configuration, and troubleshooting steps.
